What is the first thing that comes to your mind when you think about the safety of data? Most of the people think about antivirus programs. But even the most powerful antivirus programs can’t protect your files. They just keep them safe from viruses, but what about the protection of data in them? That’s when you should use encryption.
So, let’s start as usual, by defining the encryption. To encrypt something means to transform it into some form of text that only people with the key them can read it. If someone has the key then he can decrypt that text and read the original form of it. Encryption of some important data dates a long way back in history when people, especially when in war, used different ways of turning messages upside down and preventing the enemy from discovering their war strategy. When encryption first appeared it meant only changing the order of letters or switching some letters with numbers and similar stuff. Anyone who knew about that way of encryption was able to decrypt the message. But with computers we got a more complex way of encryption. There are two forms of encryption: public key encryption and private key encryption.
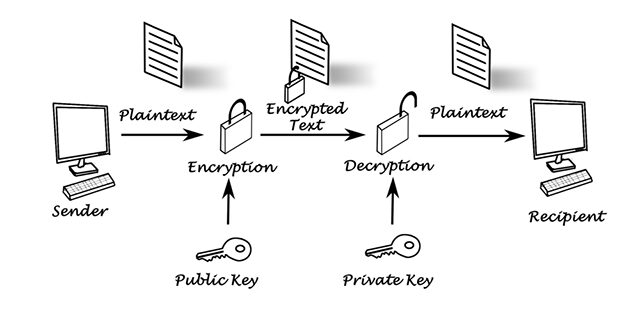
- Public Key Encryption
In public key encryption some person can encrypt some text with his key and then send it to other person with private key. Then that other person can use that key to decrypt the message and see what is in there. The most important thing about public key encryption is to realize that public key is used only for encryption and private key is used only for decryption. If you have public key you can encrypt the message but can’t decrypt it. On the other hand, if you have private key you can only decrypt the message you get but you couldn’t encrypt the message back.
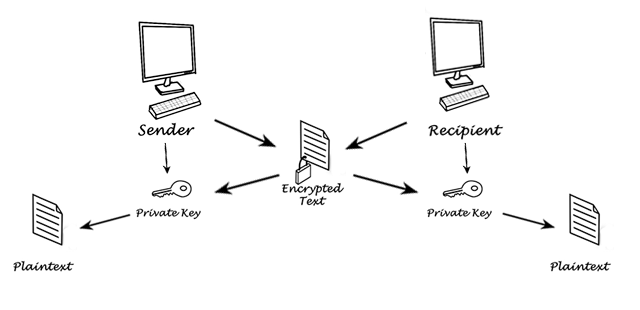
- Private Key Encryption
In private key encryption both persons have the key and can do both encrypting and decrypting of some text.
Encryption of some important data is a very big part of our technology. For example, every time you do some money transactions on internet you actually use encryption and decryption. Without that, hackers could easily steal all your important data. Some of the main benefits of encryption include:
- Flexibility – if you have some encrypted data with you and a key to decrypt it then you can access some important information everywhere. You can put that file on your laptop, PDA, email, cloud server or on some USB stick. And if you lose that no one will be able to see what is written in that file because they don’t have the key.
- Power – the power of encryption allows companies to reach the highest level of security possible. You can encrypt every little important data about your company and no one will be able to break it.
- Transparency – if you send some important information about your company to someone else and you don’t encrypt it then someone could steal that information and hurt your company. If you encrypt every important information then you will be able to feel safe about your business.
To successfully encrypt some important information of yours you will have to use one of possible algorithms. Keep reading to find out more about them.
Encryption algorithms
When you are encrypting something you should always use algorithm for it. If you search for an algorithm you will see that there are really lots of options and each one of them is different. So, how to pick the right one? Don’t worry, below you can find algorithms that are safest and mostly used by people.
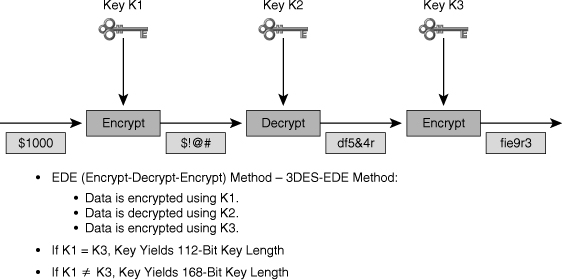
- 3DES
DES encryption algorithm first appeared in 1979. And since then it developed a lot and today we have Triple DES (3DES), a new technology based on that fist DES algorithm. Current size of 3DES algorithm is 168-bits and you know what the rule is –“More bits, better protection”. In most cases 3DES algorithm will be enough to protect your data but if it you have some really important information I recommend using some other algorithm because advanced hackers could crack your 3DES encryption key in less than a week.
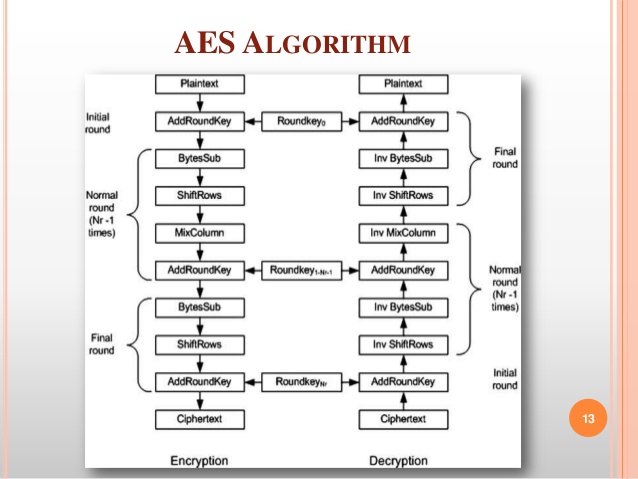
- AES
AES (Advanced Encryption Standard) is an algorithm approved by the government standard of US. AES is used even more than DES and it is a lot more popular. AES key can be up to 128, 192 or 256 bits in size. If someone wants to crack your key with brute force it would take them about billions of years. Worth waiting, maybe? Probably not, but recently there were some of the more advanced examples of attacks that are a little faster. Still, AES is probably the best choice for you because it offers really strong protection, high speed and doesn’t consume much memory.
- ECC
Elliptic Curve Cryptography is another very powerful type of encryption. It is maybe even the most powerful but isn’t not used so much because people still don’t understand it perfectly. A big company that supports this type of technology is NSA (National Security Agency) and that has to mean something.
- RSA
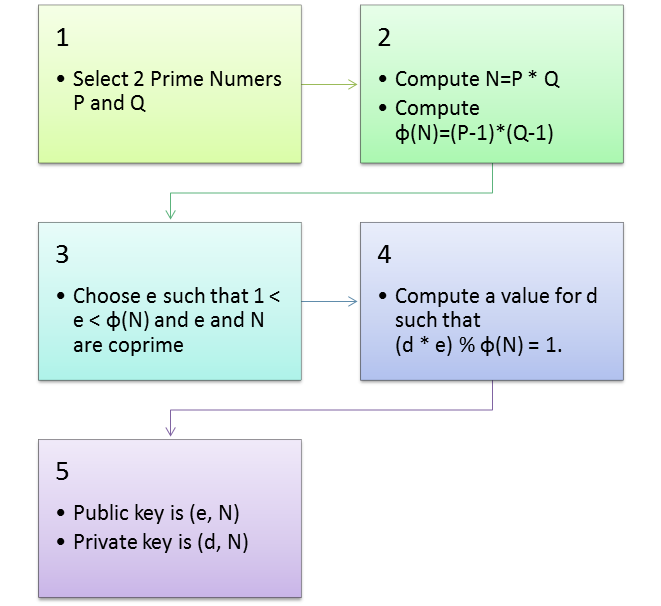
RSA is an algorithm that appeared in 1977, along with DES. It’s not enough just to have a public key to encrypt some message. Since that key is based on two prime numbers you also need some knowledge in prime numbers to encrypt and decrypt it.
Encryption Tools
If you want to keep your data safe then simply download some encryption tool and get on with it. But how to know which tool is right and what algorithm it supports? Again, don’t worry because I got you covered. Here is a list of five best encryption tools (random order).
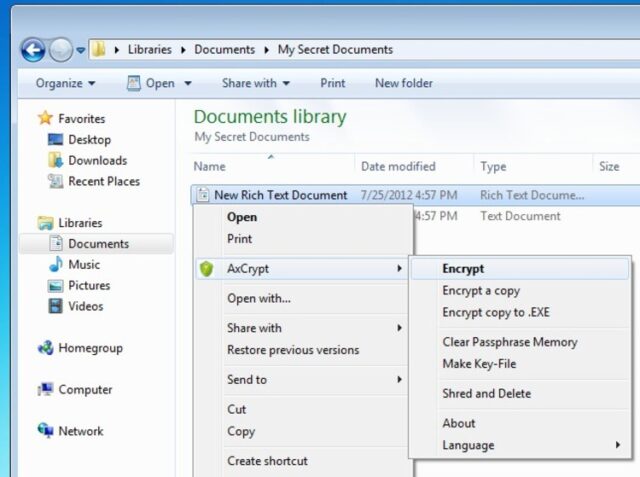
AxCrypt is a great encryption tool for Windows platform. It is GNU GPL licensed and it is based on open source code. AxCrypt is simple to easy and very efficient. To encrypt files you can simple right click on some file and encrypt it. You can also create a scheduled encryption time. With that scheduled encryptions you have the option to encrypt some files to a fixed period of time after which it will automatically be decrypted. You can also encrypt it until a certain person comes with a key and decrypts it. Great thing about AxCrypt is that when someone decrypts it and gets the information they need it can automatically encrypt itself again. AxCrypt is based on 128 bit AES (Advanced Encryption Standard). Like I mentioned above, AES is completely safe from brute force attacks and it is very successful against all other forms of cracking attempts.
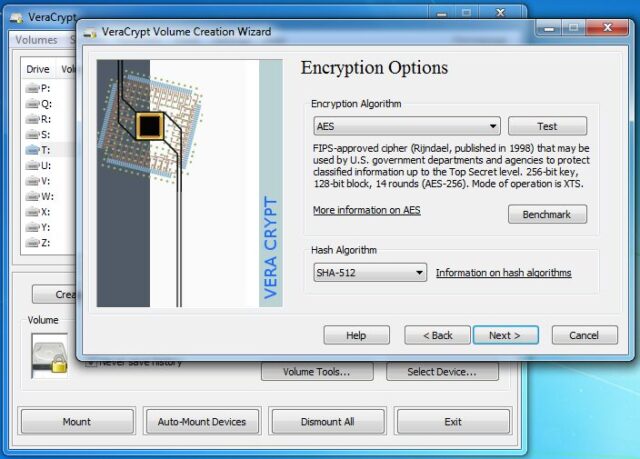
Maybe you heard about TrueCrypt. TrueCrypt was one of the leading encryption tools for a long time but its development suddenly stopped and it became very vulnerable and unsafe. VeraCrypt is a successor of TrueCrypt. In VeraCrypt everything that was ever wrong with TrueCrypt is fixed. It supports Windows, Linux and OS X. It is based on AES and has some excellent features like support to create encrypted volumes inside other encrypted volumes. It is constantly developing and gaining lots of security improvements with every update.
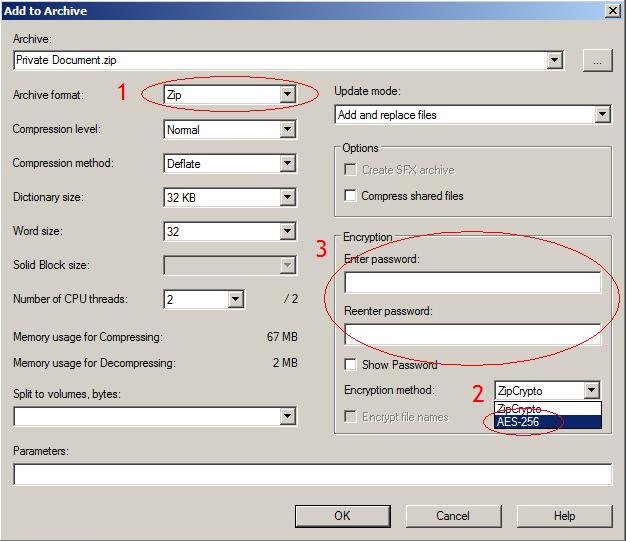
You probably heard about file archiver called 7-Zip, a good alternative to WinRAR. But, did you know that it can also serve as a strong tool for encrypting data? You can get 7-Zip for free and it supports AES encryption with 256 bits. There is a complete official Windows version along with unofficial Linux and OS X versions. Files encrypted with 7-Zip are very secure and can be decrypted with a key. Interface and design of 7-Zip is not quite good like with the others on this list but it is still very easy to use and will give you the security you need.
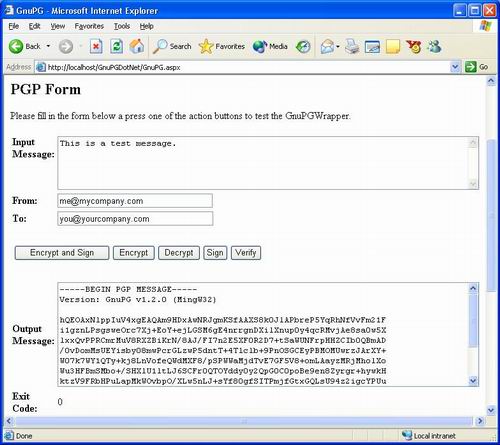
GnuPG (GNU Privacy Guard) is an implementation of another encryption and decryption program called Pretty Good Privacy (PGP). When you download this program you can get yourself a simple version that uses command line but you can also use different interfaces that will help you to figure where every command is. GnuPG can encrypt everything you want. You can encrypt emails, files, folders or the whole volumes. This program also supports some of the powerful features like possibility of multiple encryption and some other stuff.
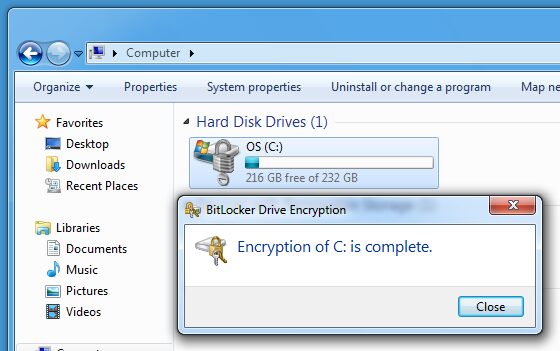
You can find BitLocker on your computer, if you use Windows. BitLocker is a built-in features of Windows Vista, Windows 7 and Windows 8. It is based on AES encryption with 128 or 256 bit size. You can encrypt the whole volumes of your computer with it and encrypt external volumes and virtual drives. You can encrypt everything with a simple password, USB key or with TPM (Trusted Platform Module). BitLocker is very easy to use and will effectively do its job.
Encryption history
I mentioned in the beginning that encryption was used a lot before computers. In fact, the first appearance of encryption was in 700 B.C. Spartans used scytales. Scytales are a wooden rods where sender would place a parchment with some message on that rod. When the receiver would tighten that parchment around his scytales he was able to read the message. Funny how the whole concept of encryption started with this.
I could mention all the tools other people used in that time and in wars that came after that but I see no point of that. Every civilization had its own way of preventing some secret messages to reach the enemy. Instead of naming all of that I will jump to 1467 when Leon Battista Alberti invented Alberti cipher. That cipher contained two metals with mixed letters of alphabet and lots of rotation options.
300 years later we got Jefferson wheel. It was invented by a person with the last name Jefferson. You would never guess that one, right? Anyway, Thomas Jefferson was a secretary of state for George Washington and his device contained 26 wood pieces placed to an iron spindle. When you would turn that wooden pieces you would scramble or unscramble words. It was widely used by US army at that time and even between 1923 and 1942.
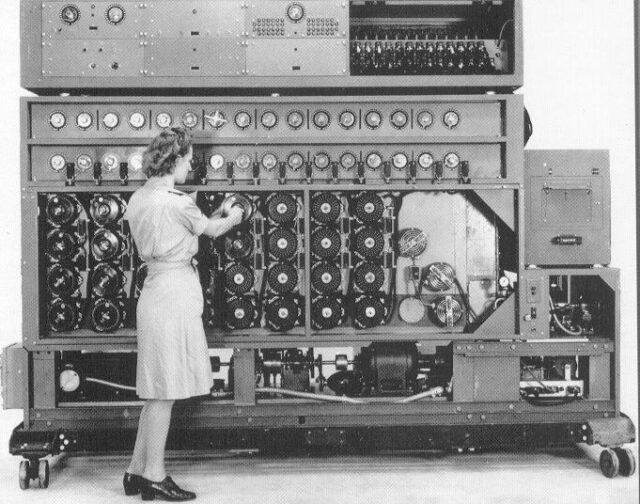
Polish cryptanalysts invented Enigma in 1943. Decryption establishment Bletchley Park formed by Britain was trying to decrypt that messages for a long time. And after a long time of trying a talented team led by Alan Turing built the Turing’s Bombe machine and cracked the code of Enigma. It helped in beating Nazis in WWII.
In 1961 a first computer password appeared along with username and was used for use authentication. But only five years later in 1966 a bug appeared and anyone who was logged in to the CTSS (Compatible Time-Sharing System) was able to see all the CTSS passwords.
And like I mentioned in the paragraph about encrypting algorithms, in 1970 we got DES. It was used for almost 20 years but then in 1998 EFF (Electronic Freedom Foundation) broke the whole key in 56 hours and later they even did that for 22 hours.
Do you know what Videocipher II is? Don’t worry, its way behind us but it is useful to know that in 1985 Cinemax, HBO and other TV houses started to use that system in a TV satellite scrambling system that was based on DES. But few years later some studies discovered that less than 10% of dish owners actually paid for that service.
In 1995 a hacking culture developed and encryption of data became more important. Just two years later we got AES developed by National Institute of Standards and Technology. Just like I mentioned with almost every encryption tool above, AES is still widely used today and it is the most powerful encryption algorithm. CAPTCHA also appeared the same year. Online spam increased a lot and AltaVista developed a filter that generated an image of random letters or numbers that only humans could read.
And in the last decade or so hacking increased even more. Identity theft appeared, along with state-sponsored hacking and in 2011 there were so many hacking actions that 2011 was called “Year of the hacker”. About 70 million of Sony PlayStation users were hacked that year, 200,000 Citibank customers were hacked and about 600,000 Facebook account were hacked every day.
Since then people began to realize the importance of encryption and stronger passwords even more. It is important for you to encrypt your personal files and data with a strong encryption tool and to use a powerful passwords for your accounts. To learn more about passwords read my article – Security World – Password Analysis.
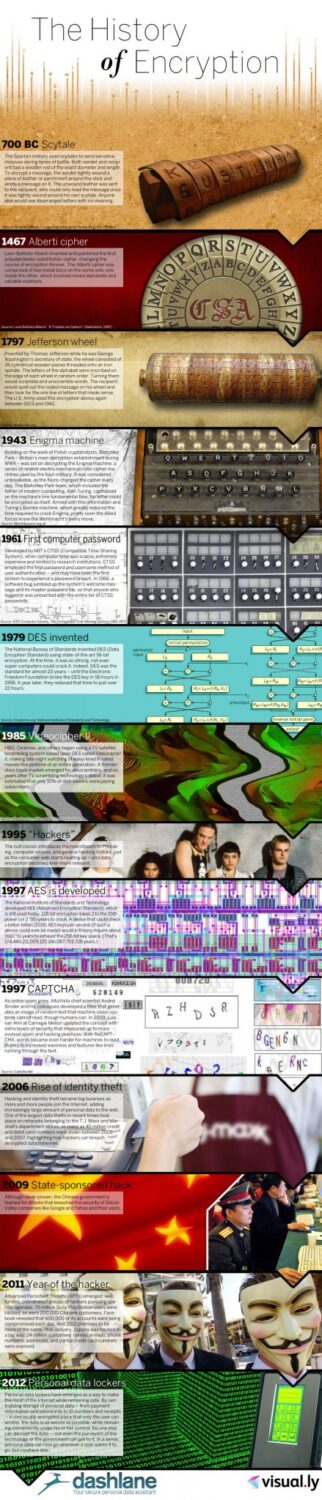
To find more details about the history of encryption check the infographic below. Enjoy!